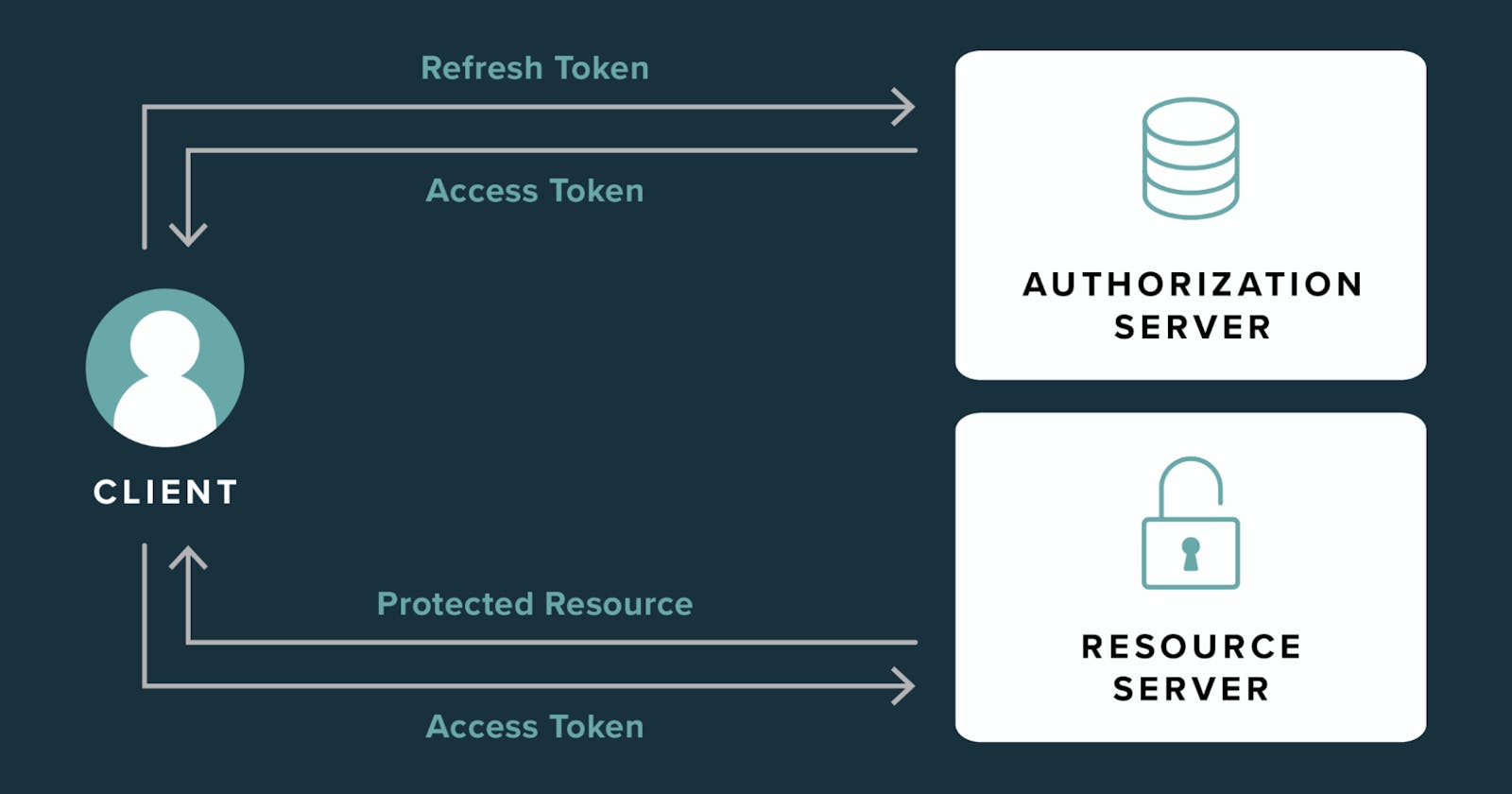
Token-based authentication is a widely adopted method for securing web applications. It involves the use of access tokens and refresh tokens to verify the identity of users. In this article, we will delve into the concepts of access tokens and refresh tokens, their roles, and how they contribute to a secure and seamless user authentication process.
Access Tokens
Access tokens are short-lived, temporary tokens that are issued by an authentication server upon successful user authentication. These tokens serve as a proof of the user's identity and are included in the headers of HTTP requests to access protected resources on a server.
Characteristics of Access Tokens:
Validity Period: Access tokens have a limited lifespan. They are designed to be short-lived to enhance security. Once they expire, the user needs to re-authenticate to obtain a new access token.
Scopes: Access tokens often include information about the specific permissions (scopes) granted to the user. These scopes determine what actions the user is allowed to perform.
Stateless: Access tokens are typically stateless, meaning that the server does not store information about them. The server validates the token by checking its signature and expiration time.
Refresh Tokens
Refresh tokens are long-lived tokens that are used to obtain a new access token after the current access token expires. They are securely stored on the client side and are only exchanged with the authentication server.
Characteristics of Refresh Tokens:
Longevity: Refresh tokens have a longer lifespan compared to access tokens. They are used to request a new access token without requiring the user to re-enter their credentials.
Usage: Refresh tokens are only exchanged with the authentication server. They are not included in requests to access protected resources. This reduces the risk associated with exposing long-lived tokens.
Revocation: Refresh tokens can be revoked by the server, providing an additional layer of security. If a refresh token is compromised or no longer needed, it can be invalidated.
Token-Based Authentication Flow:
User Authentication: The user provides their credentials, such as a username and password, to the authentication server.
Token Issuance: Upon successful authentication, the server issues both an access token and a refresh token. The access token is used to access resources, while the refresh token is securely stored.
Access Token Usage: The client includes the access token in the headers of requests to access protected resources on the server.
Token Expiry: The access token eventually expires. When this happens, the client can use the refresh token to request a new access token without requiring the user to log in again.
Refresh Token Exchange: The client sends the refresh token to the authentication server to obtain a new access token. If the refresh token is valid, a new access token is issued.
Security Considerations:
Token Storage: Both access and refresh tokens must be securely stored on the client side. Techniques such as HTTP-only cookies can be used to mitigate the risk of token theft.
Token Rotation: Regularly rotating refresh tokens enhances security. This prevents the long-term use of a single refresh token, reducing the risk associated with compromised tokens.
Token Revocation: The ability to revoke refresh tokens provides a way to respond to security incidents. Revoked tokens become invalid, even if they haven't expired.
Token Transport: Ensure secure transport when exchanging tokens. HTTPS should be used to encrypt communication between the client and the authentication server.
Conclusion:
In conclusion, access tokens and refresh tokens play crucial roles in the token-based authentication process. Access tokens provide short-term access to resources, while refresh tokens facilitate the renewal of access tokens without requiring repeated user authentication. Understanding and implementing a secure token-based authentication flow is essential for building robust and reliable web applications.
By incorporating these concepts into your authentication mechanism, you can enhance the security of your application while providing a seamless experience for users.